
perspectives
Ransomware: What Every Growth Company Needs to Know


One of the most common – and costly – mistakes business leaders can make today is to assume that their company won’t be the target of a ransomware attack. Executives of high growth companies might presume that their business is too small to appeal to cyber criminals or that they operate within an industry that is unlikely to be the subject of a cyberattack. These are dangerous misconceptions because they leave companies vulnerable to attacks, which have become increasingly commonplace for businesses of all sizes that serve industries of all types. As ransomware expert Peter Marta, Partner at Hogan Lovells, says, “if you have a computer and if your company uses a computer, you’re a likely victim of a ransomware attack.”
To help executives across Spectrum Equity’s portfolio prepare and protect their businesses from ransomware attacks, we invited four professionals with deep expertise and operational acumen managing cybersecurity and cybercrime for companies to offer guidance on steps every executive team should take to prepare for and respond to ransomware attacks.
The event included perspectives from law and law enforcement, technology, and insurance to provide a cross-functional approach to preventing and managing attacks. Peter Marta joined Christopher Hudel, Chief Technology Officer of Spectrum Equity-backed Spreedly, Richard Jacobs, Assistant Special Agent in Charge of the Cyber Branch at the FBI, and Daniel Burke, an insurance expert and Senior Vice President & Partner, Woodruff Sawyer. The panel offered sound, strategic advice and tangible solutions for any executive.
We found their insights invaluable and have synthesized their guidance for you with the hope that with more knowledge and preparation you can better protect your companies.
~ Sanjay Tiwary, Chief Technology Officer, Spectrum Equity
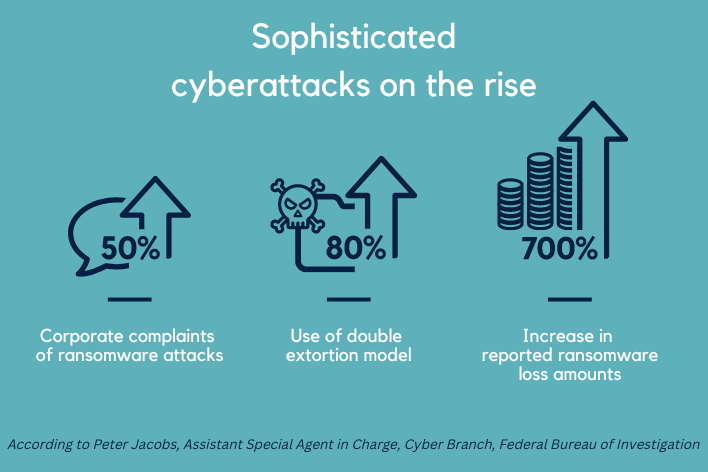
Ransomware by the Numbers
Common Attacks and Vulnerabilities
According to the FBI’s Richard Jacobs, the most common ways businesses are attacked are through email phishing and unprotected network ports, including remote desktop. Increasingly, attackers are also targeting vulnerable software and vendors to get access to hundreds or even thousands of victims at once. To protect your business, Jacobs recommends focusing on vendor risk management and conducting regular risk assessments.
The FBI has also seen a dramatic increase in the “double extortion” model, whereby cybercriminals steal data and demand payment for not releasing the data publicly, in addition to ransom for decrypting and returning the data. “We estimate that 80 percent of all ransomware attacks now use double extortion,” said Jacobs.
The Best Defense is a Plan
If we learned one thing from our conversation, it’s that there is a high probability that your business will be the target of a ransomware attack. All four of our expert panelists stressed that the best defense against ransomware is preparation. A key component is developing an Incident Response Team and plan, which is reviewed regularly with the executive management team and board of directors, so that you can address the attack and return to normal operations as quickly as possible.
How to Form an Effective Incident Response Team & Plan
I. Involve Key Players and Don't Ignore Communications
Marta of Hogan Lovells recommends creating a small Incident Response Team of key players, including both internal and external legal counsel, employees who cover the functions of the Chief Security Officer or Chief Information Officer, and the Chief Technology Officer. He stressed not to ignore communications. “Communications is critical and often difficult, so make sure you manage the outreach to your customers and important stakeholders such as employees, investors, media, and regulators, if applicable. Make sure you have communications templates created in advance.”
II. Have Cybersecurity Insurance in Place
“Cybersecurity insurance can be incredibly helpful in responding to ransomware events,” said Daniel Burke from Woodruff Sawyer. “However, because insurers are paying out more losses than premiums they’re taking in, it’s become a very challenging insurance market cycle. The process of getting insurance is much more robust and companies have to put in place a number of specific technical controls to meet the right thresholds for insurance.” Controls may include multifactor authentication, segregated backups, and encrypted backups.
In preparation for an attack, Burke advises companies to take the time to understand their policy and have a point person, preferably legal counsel, for working with the insurance carrier.
“Make sure your counsel understands your cybersecurity insurance policy, regularly engages with the response plan, and has pre-approved cyber vendors in place that can respond quickly when an incident takes place,” Burke adds.
III. Prepare The C-Suite
Above all else, make sure you have had the conversation at the most senior levels of the company about whether your firm would consider paying a ransom and what the circumstances would be to do so. When a company is attacked, these questions get escalated to the C-Suite and board within hours, so it is best to have a plan around who is authorized to make a decision and the framework for making a decision.
IV. Partner with Law Enforcement
Reducing systemic cyberthreats involves both the private and public sectors. Jacobs of the FBI recommends partnering closely with law enforcement, especially before an attack happens. “Your local FBI field office will connect you with cybersecurity experts and resources who can provide mitigation techniques and guidance.”
Jacobs also recommends involving the FBI in planning exercises to better understand how law enforcement can support your business. “The day of a ransomware attack when you are under stress and managing a crisis, you want to already understand how the FBI works and what we can do to support you.”
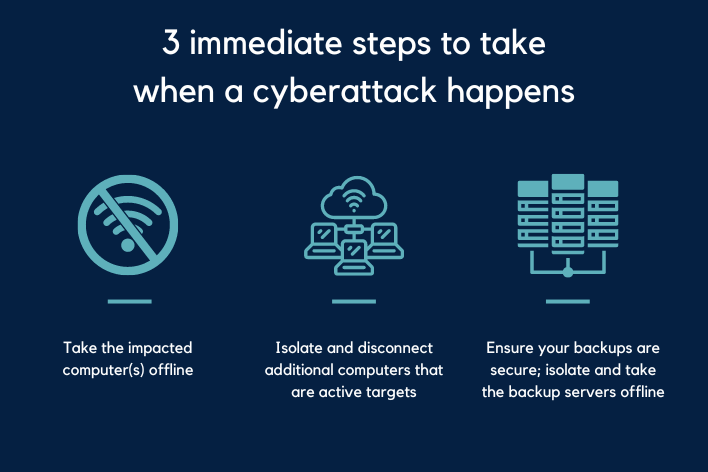
Navigating the Incident
When a cyberattack happens, there are three immediate steps you should take to minimize the damage and return business operations as soon as possible, says Christopher Hudel at Spreedly.
Negotiation + Payment
It’s well known that the United States doesn’t negotiate with terrorists, but what about in the case of cybercriminals? The guidance is murky and evolving. There is no law in the U.S. that says it’s illegal to pay ransom, but in 2020 the U.S. Department of Treasury updated its guidance to say that all entities involved in paying a ransom to sanctioned entities or individuals, including banks, forensics firms, law firms, and insurance companies were subject to penalties.
However, Treasury’s guidance is meant to incentivize businesses to address their own vulnerabilities and work closely with law enforcement. “We haven’t had a scenario yet when a company was penalized for paying ransom, but that’s because the Treasury Department looks favorably on companies that have done their due diligence, assessed their vulnerabilities, formed an incident response team and plan, and partnered with the FBI,” said Marta.
“It’s complex from a law enforcement perspective,” adds Jacobs. “The reason we have so many ransomware attacks today is because so many companies are deciding to pay, thus fueling the problem.”
All four panelists have seen a range of responses, from not engaging with a threat actor to paying the ransom. There may be situations where a company has no choice other than to pay. Ultimately, the decision to pay or not pay ransom rises to the highest level of the company.
Burke from Woodruff Sawyer stressed how important active negotiation is for managing a ransomware event, primarily to extend the time window for initiating your incident response plan, including assessing your backup and involving law enforcement. If the decision has been made to pay, a negotiation strategy advised by your experts can help lower the final ransom amount.
Prevention + Hygiene
The panelists all stressed that it’s important to acknowledge that you will likely become a target of ransomware, so make sure you have additional protections in place. They recommended basic cybersecurity hygiene, awareness, training, and planning to ensure your company’s preparedness for an attack.
